PlayerPrefs are stored in the registry. What that actually is and how its contents can be extracted is today’s topic.
In this blog, the Windows registry is introduced; followed by a small guide on how to extract some of its contents into a text file.
What is the Windows registry?
The Windows registry is a collection of databases of configuration settings in Microsoft Windows operating systems. These configuration settings include information and settings for software programs, hardware devices, user preferences, operating system configurations, and much more.
When a program is installed, a new subkey containing settings like a program’s location, its version, and how to start the program, are all added to the Windows registry, and others that may interact with it. (cf. [https://www.computerhope.com])
In many ways, the registry can be thought of as a kind of DNA for the Windows operating system.
(cf. [https://www.lifewire.com])
What is the Registry Editor?
To view and make changes to the Windows registry, the Windows Registry Editor (also known as Registration Info Editor or Registration Editor) may be used, as shown in Figure 1. The Registry Editor allows users to view all keys and values that are in the registry, as well as to change any Windows, program, or driver values.
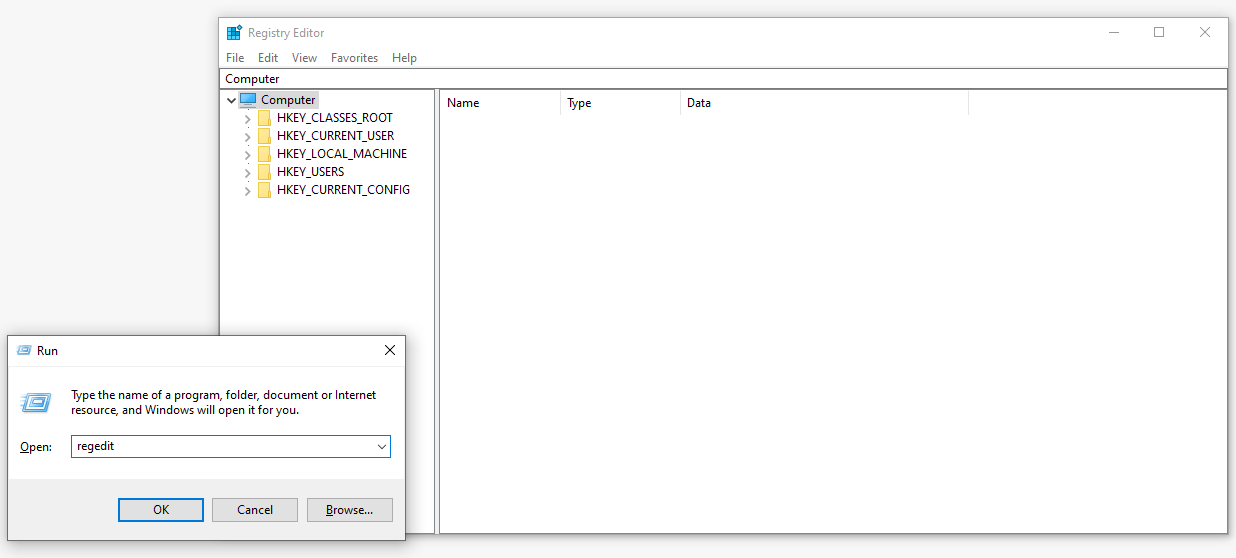
There are five so-called registry root keys (also known as hive names) in this particular registry. Each key stores information about a certain group of values, as shown in Table 1.
| Root Key | Description |
| HKEY_CLASSES_ROOT (HKCR) |
Describes file type, file extension and OLE* information
|
| HKEY_CURRENT_USER (HKCU) |
Contains settings of the user who is currently logged in.
|
| HKEY_LOCAL_MACHINE (HKLM) |
Contains information about installed hardware and software settings.
|
| HKEY_USERS (HKU) |
Contains information about all log-able users, including both generic and user-specific information.
|
| HKEY_CURRENT_CONFIG (HKCC) |
Contains details about current configuration of attached hardware.
|
| HKEY_DYN_DATA (HKDD) |
Contains plug and play (= hardware detection) information. Only used in Windows 95, 98 and NT.
|
Table 1 – Root Keys
* Object Linking and Embedding: a method of sharing information between applications. (cf. [https://www.computerhope.com])
Physically, the SAM, SECURITY, SOFTWARE, SYSTEM, and DEFAULT registry files (among others) are stored in the %SystemRoot%\System32\Config\ folder. (cf. [https://www.lifewire.com])
What can the Registry Editor be used for?
Making changes to registry values may solve a problem, answer a question, or change a program in some way; examples:
- Automatic Login
- Preventing programs from stealing focus
- Changing a Product Key
- Faking a blue-screen
- Checking the PC’s BIOS settings
The registry is always accessed by Windows and other programs. When users make changes to any setting, respective changes are also made to the appropriate areas in the registry (Sometimes they require a computer reboot, though). (cf. [https://www.lifewire.com])
Extracting Data from the registry
While it is always possible to navigate through the Registry Editor to find a certain value that can be then written down for later use, it makes more sense to do this task automatically. Windows has a built-in utility tool for that: Reg.exe.
Reg.exe provides operations that enable users to view or configure registry entries on local or remote computers (remote operations have some limitations, though). (cf. [https://docs.microsoft.com])
One operation in particular is of importance for this topic:
Reg export KeyName FileName [/y]
‚KeyName‘ specifies the full path to the desired registry value and ‚FileName‘ spcifies the full path of the created file. The ‚/y‘ option makes sure to overwrite an existing file if it had the same name as the given FileName. (cf. [https://docs.microsoft.com])
Put into practice
To execute the export operation two variables are needed: a KeyName and a FileName. The KeyName has already been found in the previous blog: „HKEY_CURRENT_USER\Software\DefaultCompany\Reinforcement Learning“ (which needs to be put under quotation marks because of empty spaces). As for the FileName: it can be any location and any name, so I choose C:\RL\score.txt for this case. Executing the full command yields the desired results, as shown in Figure 2.
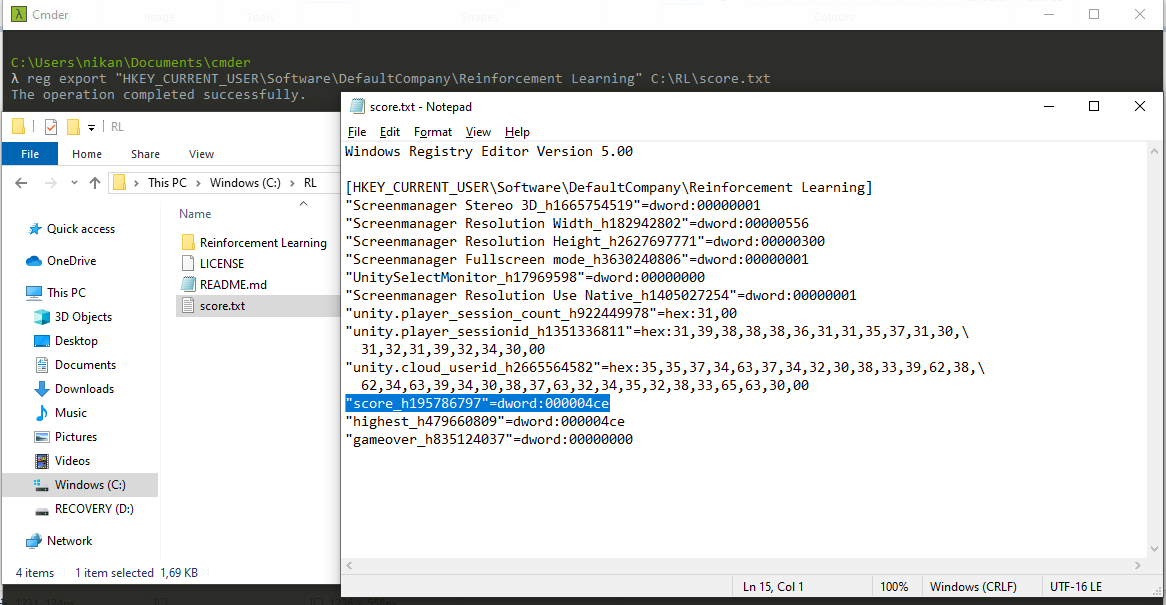
Well, now it is clear how to export the system’s DNA into a text file. It is not clear what I plan to use it for, however. That will be the subject of the next blog.
Sources
[https://www.lifewire.com]
What is the Windows registry? Windows Registry: What it is & what it’s used for. 2019. https://www.lifewire.com/windows-registry-2625992 (04.11.2019)
[https://www.computerhope.com]
Registry. 2019. https://www.computerhope.com/jargon/r/registry.htm (04.11.2019)
OLE. 2017. https://www.computerhope.com/jargon/o/ole.htm (04.11.2019)
[https://docs.microsoft.com]
Reg. 2016. https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-R2-and-2012/cc732643(v=ws.11) (04.11.2019)
Reg Export. 2016. https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-R2-and-2012/cc742017%28v%3dws.11%29 (04.11.2019)